Criminals rely on human error
Phishing is a popular form of cybercrime because it is effective. Email provides direct access to you through your smartphone, laptop, tablet, and computer. Whether a large-scale or more targeted phishing email campaign, successful email-based attacks are disruptive.
This article focuses on practical steps to reduce human error and loss events.
Phishing Email Explained
Phishing is the attempt to acquire information such as usernames, passwords, and financial details by pretending to be a trustworthy entity in an electronic communication. Creating a false sense of urgency is a common trick of phishing attacks and scams. Spear Phishing is where an attacker uses information about employees and the company to make the targeted phishing campaign more persuasive, realistic, and effective.
The simple reality is that criminals rely on human error. For email attacks to succeed, someone needs to take the bait. Cybercriminals utilize social engineering techniques to manipulate human emotions and trigger a response. Phishing emails are common entry points to gain initial access to business networks for the deployment of ransomware.
For the same reason legitimate businesses use email, criminals know there will always be a percentage of people who will error and take the bait. It can feel overwhelming given that we, as the targets, need to be right all the time while the attackers only need to be right once.
 Criminals promote their products and services to you through phishing email campaigns.
Criminals promote their products and services to you through phishing email campaigns. The consequences of taking the bait can range from insignificant to detrimental. Loss events range from a few hours of downtime to tens of thousands of dollars drained from bank accounts. These incidents occur daily, and even savvy business people take the bait.
Phishing emails position you for failure because criminals rely on human error.
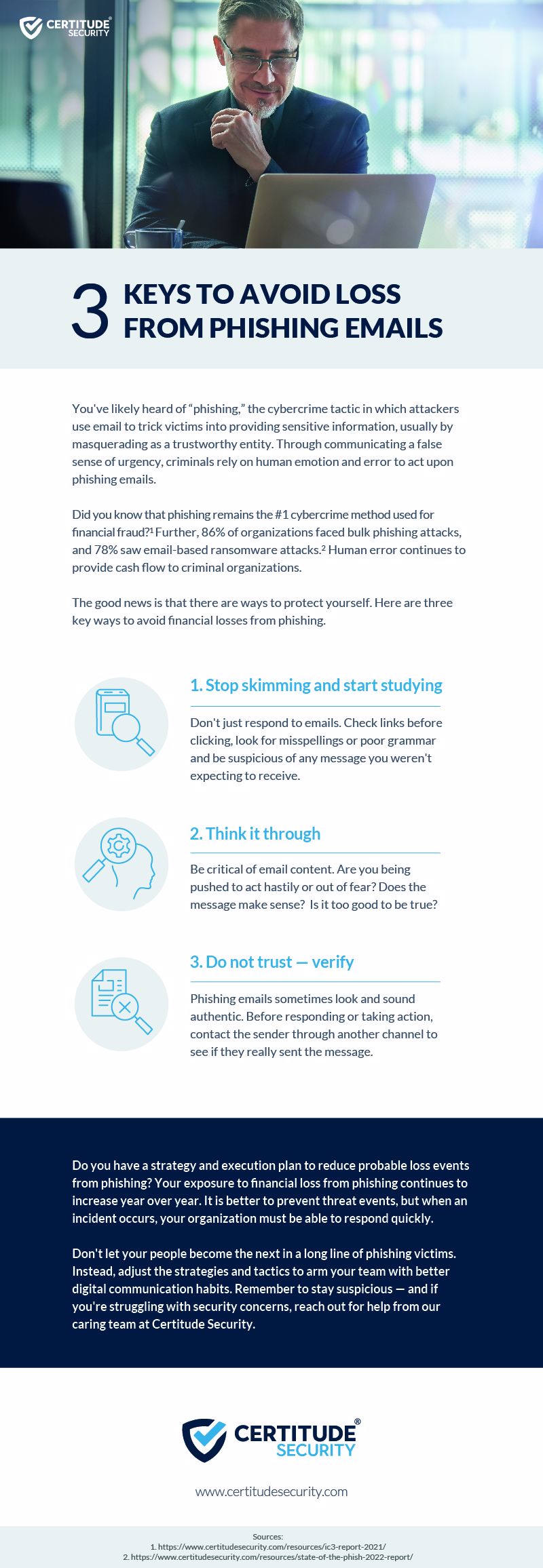
The good news is that small steps can reduce these email-based attacks to protect your data, devices, and people at work and at home. Here are three practical cybersecurity awareness training tips you can use to identify and avoid the costs of malicious phishing emails:
#1 Stop Skimming and Start Studying
We receive so many emails that we’ve conditioned ourselves to skim messages and make quick decisions. But when we do this, we do not pause to think. There are clues above and below the surface of the message that can alert us to things that aren’t right.
For example:
“From” addresses, URLs, and embedded links can masquerade as valid. Do not take these links at face value (even if a name, logo, or other identifiers seem familiar and safe). On your PC, hover over—or “mouse over”—these pieces of content and examine the info that appears (you will often see the true destination of a web address in the bottom left of your browser window).
Use a “long press” or “long click” and review the information in the pop-up window on mobile devices. If there is a mismatch between what you expected to see and what is displayed, abort, close your browser tab, and delete the email.
The greeting, content, or topic of a message might not be quite right or not entirely relevant to you. Be on alert if the tone of an email from a colleague, friend, or relative seems inappropriate or doesn’t “sound like” them.
Likewise, question the receipt of any unexpected attachment containing order confirmation, invoice, or shipping notification that doesn’t make sense based on your ordering history. Thoroughly read the message if a specific action is required; don’t just skim over the details.
Misspellings and poor grammar indicate that the email did not originate from a trusted source. This vocabulary problem is particularly true with messages that appear to be from a known, well-established individual or organization. These errors are sometimes the result of awkward translation from a foreign language, and sometimes they’re deliberate in an attempt to evade spam filters that try to block these phishing attacks.
(Learn more about phishing email concerns in this blog article.)
Review carefully any email you were not explicitly expecting to receive. Be wary of any email that triggers an emotional response, such as fear, urgency, or concern. Emails that urge you to respond quickly or act somehow (click a link now, download a file, confirm/change a password).
 Urging you to take the bait (act) is the objective of the phishing email.
Urging you to take the bait (act) is the objective of the phishing email.#2 Think It Through
After you read an email, please take a moment to digest it. Give yourself a moment to act thoughtfully rather than just reacting. Build in a delayed response to any email that contains an urgent call to take a specific action, so you can avoid skimming and responding.
Consider asking yourself a few quick questions about any email that requests a response or action that could compromise sensitive data, devices, or systems.
For example:
Was I expecting this message? — If the answer is “no,” ask more questions.
Does this email make sense? — If the tone doesn’t seem right or the information provided does not make sense, it could be a phish.
Am I being pushed to act hastily or out of fear? — If you are, this is a major red flag. Would IT ask that I reset my Microsoft Office 365 email password from a mismatched email domain or unknown website?
Does this seem too good to be true? — If you cannot believe what you’re reading, it is likely a phishing email. Your bank will not inform you via email that they need the approval to refund your account.
What if this is a phishing email? — This is a great question to ask yourself because it can help you work through what could happen if you are dealing with a phishing attack.
Could you be downloading malware that would corrupt all your files? Could you be submitting a password or credit card number to a criminal? Could you be exposing your coworkers’ private information to a criminal enterprise?
 Phishing emails lure people into urgent action. Take a moment to reflect upon the request before responding. This delay to think can reduce incidents and loss events.
Phishing emails lure people into urgent action. Take a moment to reflect upon the request before responding. This delay to think can reduce incidents and loss events. #3 No Trust, Verify
It is critical to remember that, with phishing scams, things are never what they seem. The reality is that a message can look and sound legitimate but still set off a warning bell.
It is common to receive an email from someone for the first time, especially if they are outside your organization. When you get an email from someone you don’t recognize or that Outlook identifies as a new sender, take a moment to examine it extra carefully before proceeding.
For example:
An email from a corporate IT address that tells you to download new security software can seem trustworthy. It appears accurate and is on topic. But would that be the process your IT department or IT provider would follow?
Suppose reading and thinking do not result in 100% confidence. In that case, you must take extra steps to verify that you are dealing with a legitimate request before clicking a link, downloading a file, or replying with sensitive data.
Here are some easy ways to confirm that the information presented in an email is legitimate:
Instead of clicking on a link, open your web browser and type in a known, trusted URL to access the website.
Do your fact-finding instead of replying to an email or calling a number included in the message. Use an email address or phone number that you can confirm.
If you receive a questionable message from a vendor, colleague, or friend, contact them via another channel (like a phone call or text message) to ensure they sent the email.
Social engineering is the use of mental tricks to coerce you. These attacks focus on the trust that many people share. Learn more about social engineering by reading this blog article.
If you act, do not allow your embarrassment of the mistake to prevent you from providing notification. Reach out to your IT team for advice and alert them that a potential phishing threat is active on your organization’s network.
Be Cautious to Reduce Human Error
It takes just a few minutes to confirm a questionable message, whether from a coworker, customer, vendor, financial institution, or other sources.
In contrast, it can take days or weeks (or even longer) to remedy the consequences of taking the bait with a phishing email. In cases where Human Resources releases employee data to criminals, you cannot rectify the effects.
What are the consequences of not safeguarding communications?
- Loss of information containing employee, customer, and financial data.
- Loss of reputation from employees, customers, and vendors.
- Increased risk of bank fraud from false payments and illegitimate transfer requests.
- Increased exposure to business disruption and financial losses from ransomware.
Your Path Forward
Believing that spam filters and basic user training will ensure adequate cybersecurity is a common mistake. The expectation that you will respond quickly to your boss or CEO puts pressure on your mind to pause and think. Phishing emails position you for failure because criminals rely on human error.
If you feel that these three tips are not adequate for bite prevention for you and your company, we can coordinate a time to discuss your concerns. There are no silly or embarrassing questions.
Informative conversations are decision-useful and result in better outcomes.
There are occasions where we suggest you and your team adjust efforts to improve prevention. Other times, a leadership team experiences an incident and needs more urgent assistance.
Commonly, leadership teams stress and struggle to contain lost revenue and expenses from exploited weaknesses. You cannot make informed risk decisions without access to useful information.
Criminals rely on human error. We can help you.
You can change how you evaluate investments to support your business and customers. We are here to assist you in protecting your people and assets.
As a proud supporter of American companies, Certitude Security® is working diligently to inform leaders and facilitate essential asset protection priorities for manufacturers and supply chains throughout the United States.
Problem discussions can be a defining moment in your career. If you are interested in value creation, learn about SPOT-Beam™ by Certitude Security®. We look forward to helping you and your business succeed!